
Mist HTB Writeup | HacktheBox
OS : Windows. Difficulty Level : Insane
Scanning and enumeration
└─$ nmap -sVC 10.10.11.17 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-31 08:43 IST Nmap scan report for mist.htb (10.10.11.17) Host is up (0.24s latency). Not shown: 999 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1) | http-robots.txt: 2 disallowed entries |_/data/ /docs/ | http-title: Mist - Mist |_Requested resource was http://mist.htb/?file=mist |_http-generator: pluck 4.7.18 |_http-server-header: Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1 | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 30.59 seconds
HackTheBox's Mist machine presents challenges in web exploration and directory enumeration. It only has one open ports. With information obtained from the main page, it is possible to start enumeration to find a rabbit hole.
Now that we have obtained a shell and successfully acquired the file user.txt, we proceed to root the box. Once completed, we will post the full write-up here.
Reverse shell
Just look around, you will find some version numbers. Search on Google to find exploits, then use those exploits to obtain a reverse shell.
After that, remember old-school methods and search for another reverse shell. Once you have one, explore how pivoting works.
Afterwards, familiarize yourself with Impacket tools - they are your friend. Use them to learn about Active Directory and how it works. Then, you can obtain the user flag
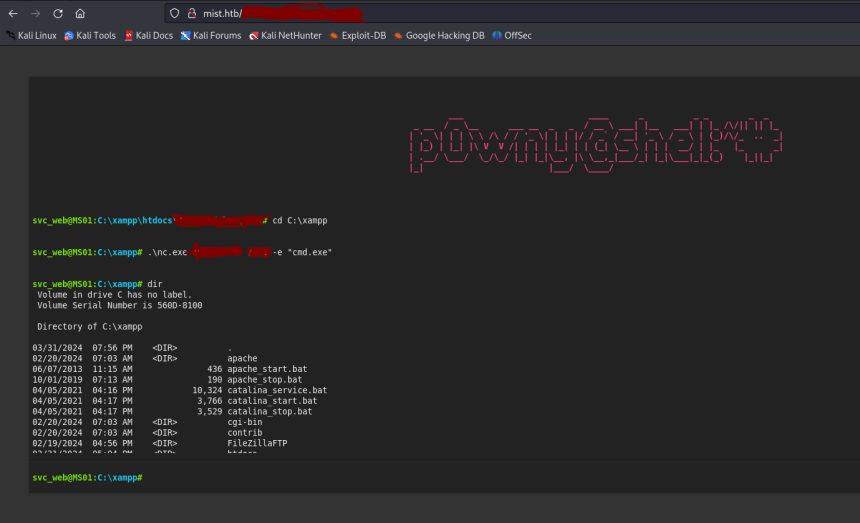
rooted

We don't post full write-ups here in this article. Instead, we provide hints, and after the box is released, we update with the full write-up.




Hack The Box Machine Breakdown: Voleur htb writeup hackthebox
📅 Release Date: 06 July 2025 💻 OS: Windows 🧠 Difficulty: Medium 🔓 Initial Acc...